Matthias Schulze, 14.10.2024
In the last blog post, we deciphered various elements of active cyber defense. We looked at technical definitions, analyzed the spectrum between defense and offense, and talked about deception. We concluded that active cyber defense might entail offense (i.e. engaging with the network of an adversary), but it does not necessarily need to. Active cyber defense might aim to preempt an imminent attack from occurring, rather than to prevent more abstract, future threats. What also became apparent is that active defense seems to entail “more” than passive defense: it employs additional tools and measures like honeypots and deceptive techniques with the aim to gather intelligence on adversary behavior. In this section of the blog post, we will look at what doing active cyber defense actually might entail.
Is active more than passive?
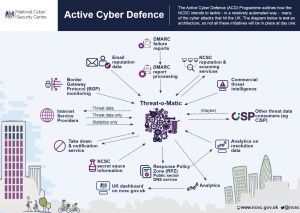
Did you know that there is one country that has an official active cyber defense program as its national policy? Allow me to introduce the UK’s “active cyber defence programme”. Although I could not spot an exact definition of the UK’s program, the gist of it seems to be that the UK National Cybersecurity Centre provides additional tools to the public to protect against the majority of cyber-threats. The UK’s “active cyber defense” program does not entail any offensive component. The program also does not include any apparent deception techniques. The focus is on prevention of “commodity attacks” which seems to mean most “commercial off the shelf” types of attacks such as automated DDoS attacks, automated vulnerability scanning, general phishing and ransomware attacks (in contrast to high-profile APT attacks). Preemption of imminent attacks is not mentioned in the documents of the program. The core components are preventive measures aimed against abstract, future threats and include:
- a takedown service to remove malicious websites
- a mail security check
- a web check service in the form of vulnerability scans of public sector websites
- a protective DNS that blocks known malicious domains, and a suspicious email reporting system as well as
- the provision of threat intelligence feeds.
So organizations essentially can set the NCSC DNS server for their devices, and it blocks web-requests to known bad sites, or they can request a vulnerability scan of their website. Neat! In other words, active cyber defense entails the active use of services offered by the UK NCSC that can be requested by organizations or being used on their own.
https://www.ncsc.gov.uk/static-assets/documents/NCSC%20Active%20Cyber%20Defence%20Programme.pdf
The insight we might gain from this is that active cyber defense means the use of more tools and services. However, does the number of tools in use say something about whether a security program is passive or active? I am not so sure.
For example, the IT security company Tenable writes:
“Active cyber defense is the practice of taking steps to prevent, detect and respond to cyberattacks before they cause damage such as:
Penetration testing: Simulating cyberattacks to identify vulnerabilities and improve security.
Threat hunting: Actively searching for malicious activity on networks and systems.
Incident response: Developing and practicing plans to respond to cyberattacks.
Passive cyber defense is the practice of implementing security measures to protect networks and systems from cyberattacks such as:
Installing security software and configuring it properly, for example, firewalls and antivirus software. Applying security patches to software and hardware to fix known vulnerabilities. Implementing security policies and procedures to educate employees about cybersecurity and reduce the risk of human error.”
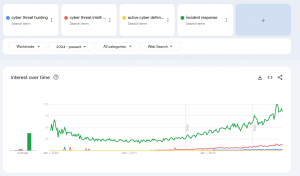
In this definition, active cyber defense entails more tools and procedures such as pentesting, threat hunting and incident response. While I get that threat hunting is a rather novel trend (see the Google Trends graphic), not many companies have the capacity to employ this. At the same time, all companies should have an incident response procedure. Incident response or management is part of international cybersecurity standards such as the older ISO 17799 (formerly BS 7799) since the year 2000. Current standards such as ISO 27001 all include incident response. The NIST cybersecurity framework also agrees that having an incident response strategy is a core element of cybersecurity that every organization should have. It is therefore no surprise that incident is the most prominent term in Google trends, in terms of search volume over the years. In contrast, “active cyber defense” (yellow) is still a relatively marginal term, even compared to more trendy topics such as “cyber threat hunting” (blue) or “cyber threat intelligence” (red) as of today [17.09.2024]
One of the inherent problems of the term “active defense” is that, qua its linguistic nature, it discredits the term it distinguishes itself from: passive defense or “normal defense” / IT-security if you want to call it that. It assumes that normal cyber-security is passive, that nothing is being done. But this is hardly true. Cyber-defense, if done well, is everything but passive. For example, what Tenable describes as passive, such as patch-management, education of employees and so forth, are quite active and involved processes. This is something that needs to be actively done all the time to succeed. Of course, one could argue that some cyber-security controls are passive in the sense that they are “fire and forget”: set up once, never touch again. Similarly, many companies still might see cyber-security as a one-time investment: buy a shiny, fancy Unified Threat Management solution once and your security and compliance needs are fulfilled. On the other side, many cyber-security vendors market their product in such a way: this is the only appliance you need. This “fire and forget approach to security” might also be present in terms of processes: Organizations might to through the initial hardening and secure configuration of networking equipment, the creation of Firewall rules or the initial configuration of group policy objects in an Active Directory Domain and then never touch them again. But I would argue that this “fire and forget approach” to cybersecurity is just wrong and a bad practice.
Most practitioners agree that cyber-security should not be a one-time investment and activity, but rather a continuous process of updating defenses to protect against the newest evolution of threats. In other words, good cyber-security should be active cybersecurity and only outdated or rather immature cyber-security policies remain passive, mostly by neglect and lacking resources. In that sense of the meaning, active defense is a security paradigm and the opposite approach to “fire and forget security”.
Active cyber-defense as continuous commitment
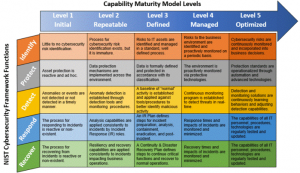
In other words, the term active cyber defense might tell us something about the active commitment, in the meaning of continuous activity, of an organization to its security. And this in turn tells us something about the maturity level of different organizations. What is that? The aforementioned NIST offers a cybersecurity maturity model that helps to determine the maturity of an organization’s cyber-security efforts, i.e. how good or advanced defense is. It distinguishes immature organizations that don’t have cyber-security policies, nor the adequate funds, operational processes and human resources from those who have and those that utilize them better than others:
Level 1 or immature organizations tend to be entirely passive and follow the “fire and forget approach” to security. There is no ongoing risk management. There are no updated asset inventories and asset protection guidelines. Maybe there is an antivirus system installed on some endpoints, but the effort is not systematic. There is no capability to detect threats in a network, no logs and sensors. There is no established incident response strategy. In practice, that means that organizations might have an IT-staff (if at all!), but its focus is on IT-administration in general and not cyber-security. It is still often the case that many IT-administrators are not trained in cyber-security because it is a different skill set and extra specialization compared to IT-administration (which is more concerned with the time-consuming upkeep and maintenance of IT-infrastructure and less so with its security). In other words, immature organizations lack security specialists that are responsible for the cybersecurity of an organization. More mature organizations tend to have IT-security specialists, in addition to IT-administrators, whose job it is to come up with a cyber-security strategy, its documentation and implementation. The cyber-security posture of too many, particularly small and medium enterprises, still resides on this level.
Where it gets interesting is between the maturity levels 3 “defined” and level 4 “managed” security. Those organizations have a cybersecurity policy and have active procedures to continually implement it. In level 4 organizations, risks to the business are proactively monitored. The same is true for the environment in the form of technical measures such as intrusion detection or prevention systems, Endpoint Detection and Response or in terms of operational components. Cyber-mature organizations tend to watch new vulnerabilities actively being published and repeatedly and actively scan their environment for these vulnerabilities. They have an up-to-date asset inventory and know what software versions run on their endpoint because they actively keep track of this. They also might employ penetration testers to actively seek holes in their security posture. Level 4 includes “active” threat management processes like having a Security Operations Center where a team of security analysts monitors real-time behavior of devices in a network, screening for alerts. It includes a response capacity to deal with security events. It includes the operational processes, adequate funds and the human resources, in the form of cyber-security analysts, that respond to alerts and mitigate them. This might include a SIEM solution that aggregates logs from all over their network environment. On the incident response side, it includes the presence of active incident response teams that follow a time-tested response strategy that can be activated once a breach occurs. All of this is active. All of this entails people doing something to increase the security of a network, instead of just idling and twisting thumbs.
Takeaway message
In other words, a high level of cyber-maturity implies active cyber-security, even though it is passive in the geographical notion of the term and might not even include a deception or even offensive component. SOC and Incident Response teams tend to focus on their network perimeter and don’t engage in offensive practices. Only the immature organizations rely on purely passive matters in the sense of their commitment to cybersecurity. So we can conclude that active cybersecurity entails indeed more tools, procedures, and practices than just passive cyber-security and most essentially, it involves a higher commitment to security. We can make the case that “active cyber defense” is a paradigm of how an organization pursues its security by actively and constantly updating it vs. setting it up once and forgetting about it. In other words, active cybersecurity does not necessarily have to imply going on the offensive or having sophisticated deceptions in tools in place, but rather just means taking security seriously and actively committing to it. In this regard, active defense is a goal and a mindset of an organization.